Businesses pay a significant premium to recover from a cyber attack, if the virtual infrastructure is affected during the incident. This is the surprising finding of a special report on the Security of Virtual Infrastructure prepared by Kaspersky Lab, based on a worldwide survey of 5,500 companies conducted in cooperation with B2B International in 2015. This may look strange, even somewhat counter-intuitive, but the explanation is rather simple.
Security of #virtual infrastructure: errors may cost. #enterprisesec
Tweet
Figures
When the virtual infrastructure is affected, enterprises pay more than $800,000 on average to recover from a security breach, the report finds, which is twice as much compared to incidents involving only physical infrastructure. SMBs experience the same pattern: On average, SMBs reported damage of more than $26,000 for an attack on their physical infrastructure. However, the involvement of virtual infrastructure in a security breach drives the cost up closer to $60,000.
The report also finds that the majority of businesses use virtual infrastructure for their most important operations. While an attack on physical nodes leads to the temporary loss of access to business critical information in 36% of incidents reported, this rises to 66% when a breach affects virtual servers and desktops.
Attacks affecting virtual environments also more frequently require additional budget on third-party expertise. Businesses have to request help not only from IT consultants, but also lawyers, risk management experts, and others.
And the reasons are…
Up to 62% of businesses use virtualization in some form, while only 56% are fully prepared to deal with security risks in their virtual environment.
The complexity of security measures in a virtual environment, as well as an incorrect perception of the threat landscape, are two additional elements that increase the cost of recovery in the virtual environment. Kaspersky Lab’s report shows that 42% of businesses believe that security risks in virtual environments are significantly lower than in ‘physical’ environments (wrong). 45% of companies report that security management in virtual environments is perceived as a problem. Furthermore, only 27% of businesses have deployed a security solution specifically designed for the virtual environment. 34% are not even aware such a solution exists on the market.
This means that if they do protect their virtual machines parks, they most likely use the client-based security solutions tailored for use with the physical devices (PCs, servers, etc.). That makes a huge impact on virtual infrastructure, even if provides a decent level of security.
Diminished advantages
Virtualization offers a lot of advantages, and the possibility to speed things up isn’t the least of them. However, these advantages tend to fade away if the virtual systems security is approached from the wrong angle.
The traditional client-based solutions used within the virtual infrastructure may put heavy strain on the hypervizor: one of the simpliest reasons is the duplication of their own resources and consumption of the physical resources. This kills the very idea of virtualization. Why talk about fast and dynamic resource allocation within an enterprise infrastructure if it crawls?
Kaspersky Lab’s own product tailored specifically for protection of virtual infrastructures uses a very different approach. Its primary idea is to reduce the resource’s drain, so that dynamic changes within the virtual infrastructure stay dynamic, without any ‘crawling’. This is achieved via the centralization of protection.
Enterprises pay over $800,000 on average to recover from a security breach affecting virtual infrastructure. #enterprisesec
Tweet
Depending upon the virtualization platform, there are agentless variants and so-called ‘Light Agents’, when every VM is equipped with a small piece of software acting in the similar way to a full-scale security agent, but without straining the server. In both cases, there is ‘the core’ – a virtual appliance installed on the host, which actually performs all resource-intensive security processing, thus providing immediate protection for every virtual machine, both existing and new. The solution also has a unified, centralized database on all threats, so there is no unnecessary data duplication. Also, there is Shared Cache, which ensures that the same file opened on several different VMs is scanned only once: The scanning engine’s initial verdict is shared within all of the environments, so unless the ‘good’ file is changed or a user requests a new scan manually, it will be considered safe and won’t be scanned again.
In recent years it’s become clear that virtual PCs (especially those with Windows installed) require protection from cyberthreats as well as physical ones. Machines may be virtual, but they are still used to work with sensitive data, and a loss can have very real and, as shown above, very costly consequences. Businesses expect virtual infrastructure to drive down their IT spend and streamline their infrastructure.
However, the survey results show expenses may exceed the benefit if the security of virtual systems isn’t approached correctly. And the right approach, in our view, is the solution that has a low impact on resources, a high detection rate, and the ability to spot suspicious activity right away, preventing security breaches in the virtual infrastructure.
The full text of the report Security of Virtual Infrastructure is available here.
 Kaspersky Security for Virtualization
Kaspersky Security for Virtualization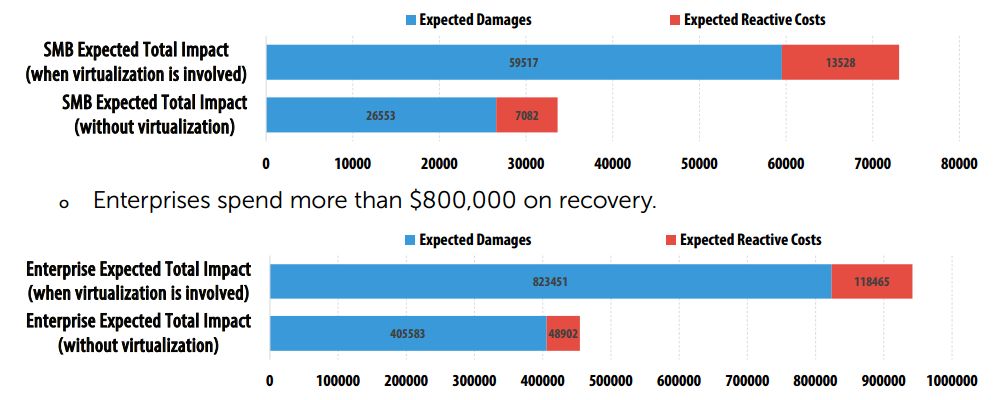

 Tips
Tips