Kaspersky Lab reported a new nasty malware family which steals accounts in Steam. While Steam Stealer attacks end-users, it is the businesses working with this platform who are the real victims.
Steam is a massively successful content-distribution platform created and operated by Valve gaming company. It has about 100 million registered users and several thousand games from various vendors available for download worldwide.
Stealing from Steam: a new #MaaS malware hits gamers and businesses
Tweet
Several years ago, Valve added distribution of various content production suites, including world-renowned Cakewalk Sonar software, game development tools, and many other professional-grade software.
In other words, the Steam platform is a major business hub with very serious finance involved.
Unsurprisingly, it attracted cybercriminals as well. According to recently published official Steam data, 77,000 Steam accounts are hijacked and pillaged every month. Steam provides multiple security tools (hardware included), but they are not exactly popular. This is a major factor in the popularity of the malware in question.
Steam Stealer is not just one piece of code, but a diverse family, offered in a malware-as-a-service business model, which has become increasingly more popular.
According to Kaspersky Lab’s researchers, Steam Stealer is available for sale in different versions, with distinct features, free upgrades, user manuals, custom advice for distribution, and more.
When it comes to these types of malicious campaigns the usual starting price for “solutions” is in the range of $500 USD. However, Steam Stealers have a ludicrously low price, commonly sold for no more than $30 USD. This makes the malware highly attractive for wannabe cybercriminals all around the world. At the same time, Steam user credentials are sold on the black market for $15 USD on average.
However, since the in-game vanity items from many titles are bought and sold for real money, criminals see a lot of opportunities there: These items may be worth thousands of dollars, regardless of their origin.
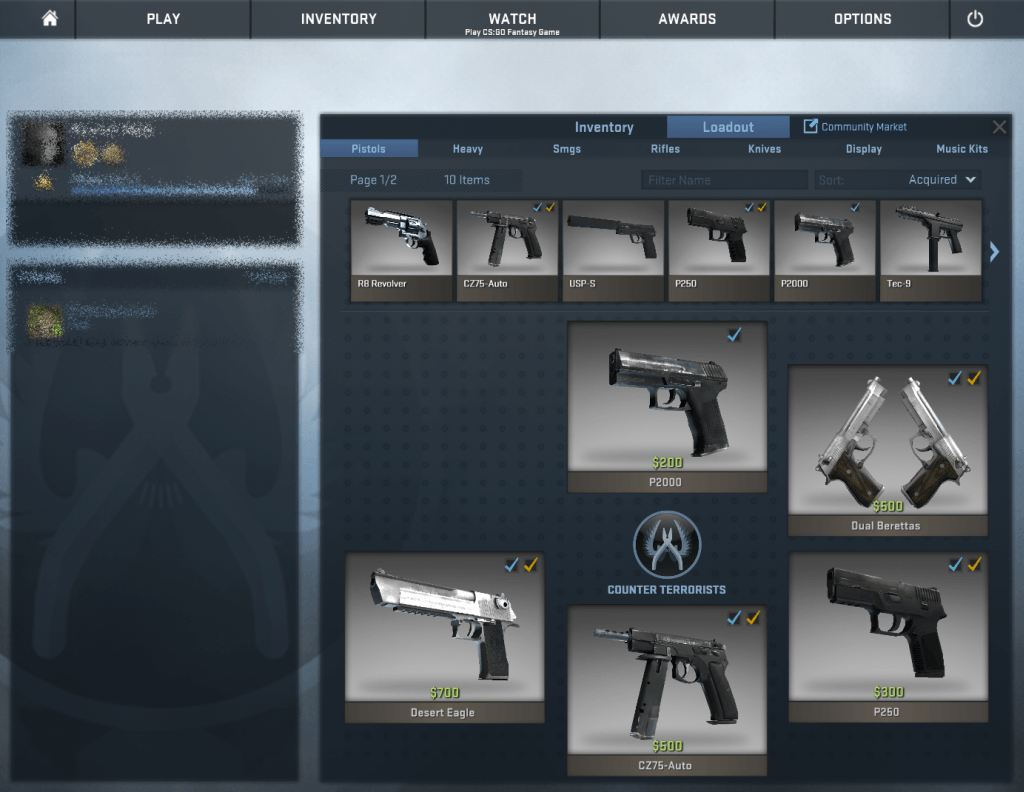
In-game items may or may not affect the gameplay, but still they are bought and sold for real money. Here’s where hackers’ interest gets ignited.
And while it is gamers who suffer first, in the end the entire gaming ecosystem is damaged, as is the game’s developer.
There is a definite parallel between gaming-oriented malware and banking Trojans: While it is mostly banks’ individual clients who get attacked, eventually banks have to conduct damage control and cover losses of their clients, if the funds get stolen.
So far, Kaspersky Lab experts have discovered nearly 1,200 samples of different Steam Stealer variants that have been attacking tens of thousands of users around the world, especially in Russia and other Eastern European countries where Steam’s platform is extremely popular.
#Security considerations should be present since the very start of the software development process.
Tweet
Kaspersky Lab detects Steam Stealers trojan groups as: Trojan.Downloader.Msil.Steamilik; Trojan.Msil.Steamilik; Trojan-psw.Msil.Steam amongst others. Targets of these trojans are largely spread around the globe with Russia, the U.S., Europe (France and Germany), India, and Brazil leading the way.
To the end-users we recommend they arm themselves with an up-to-date security solution, together with Steam’s own security measures.
At the same time, for developers of software, both gaming and non-gaming titles, our message is that security considerations should be present at the very start of the development process.
“The gaming community has become a highly desirable target for cybercriminals. There has been a clear evolution in the techniques used for infection and propagation, as well as the growing complexity of the malware itself, which has led to an increase in this type of activity. With gaming consoles adding more powerful components and the Internet of Things on our doorstep, this scenario looks like one that will continue to play out and become more complex. At Kaspersky Lab, we hope that our research will develop into an ongoing investigation, bringing a much-needed balance to the gaming ecosystem. Security should not be something developers think about afterwards but at an early stage of the game development process. We believe that cross-industry cooperation can help to improve this situation,” comments Santiago Pontiroli, Global Research & Analysis Team, Kaspersky Lab.
Check out our previous posts on security of online games:
https://business.kaspersky.com/security-of-online-gaming-business-reasons-to-care/2912/
https://business.kaspersky.com/pay-to-play-again-a-cryptolocker-variant-goes-after-the-gamers/3715/
 malware
malware

 Tips
Tips