Antispam technologies: secure mail for people and business
Fighting unwanted and often dangerous correspondence is a must for comprehensive protection of infrastructure and requires solutions which are based on effective antispam technologies.

Technology expert, Kaspersky
11 articles

Fighting unwanted and often dangerous correspondence is a must for comprehensive protection of infrastructure and requires solutions which are based on effective antispam technologies.

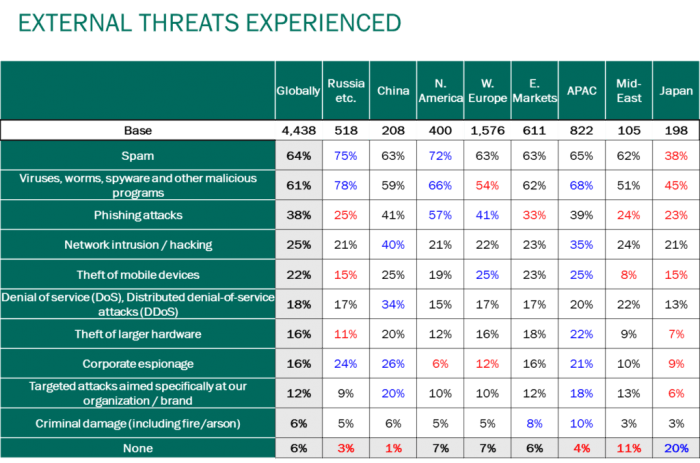
Cybercriminals frequently use spam as the primary channel to spread malware. Of course, this is something we should take care of.
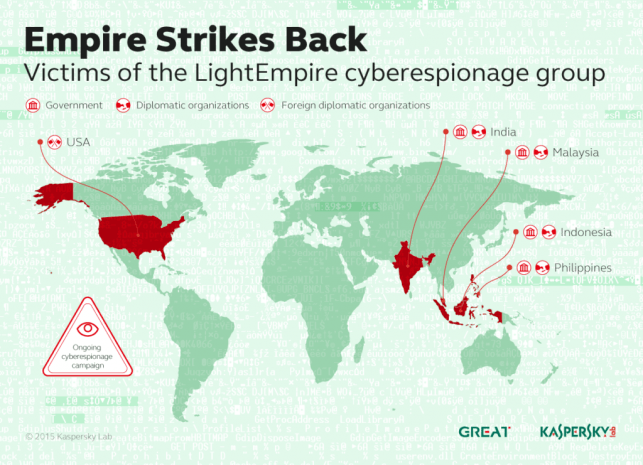
Kaspersky Lab experts have discovered a new APT campaign that targets government institutions, mainly in the APAC region. It was named “Hellsing” after the string containing the project directory name found within the attack components’ code.

Hacking and espionage are hardly crimes for the secret service, but rather are a part of their everyday work. But imagine what could happen if their tools end up in wrong hands.

The Problem One of the most effective and dangerous ways to run malicious software on a victim’s computer is by exploiting vulnerabilities in popular applications or within the operating system.

The problem Any company regardless of the level of maturity possesses some valuable information which having got into the hands unscrupulous individuals can put an end not just to the
The Problem At present, even very small companies store information that could cause irreparable damage to their financial future if it fell into the wrong hands. An example of this
As many as 4.2 million attacks using Java exploits were repelled by our Automatic Exploit Prevention system between September 2012 and August 2013. This number indicates two points. The first
The Problem We often hear from small business owners that the modest size of their companies provides them with “invisibility protection”. Employees believe that their organization and its activities are

Online shopping, online money transfers and online banking save us a lot of time and make our lives easier. However, these same technologies also make life easier for cybercriminals by

Security professionals and enthusiasts are aware of rootkits, but general audiences typically don’t know about this kind of malware, which is specifically designed to hide itself and its activity in