If you’re an active cryptocurrency user but you’re still downloading torrent files and aren’t sure how to safely store your seed phrases, we’ve some bad news for you. We’ve discovered a new Trojan, Efimer, that replaces crypto wallet addresses right in your clipboard. One click is all it takes for your money to end up in a hacker’s wallet.
Here’s what you need to do to keep your crypto safe.
How Efimer spreads
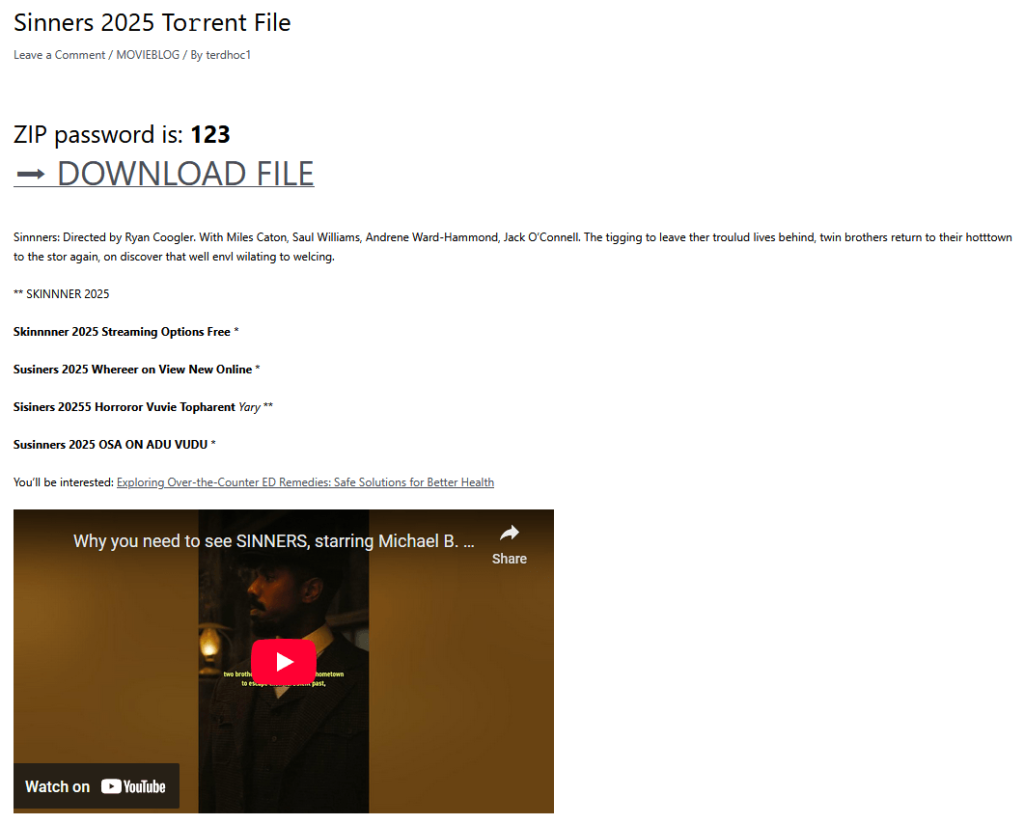
One of Efimer’s main distribution channels is WordPress websites. It doesn’t help that WordPress is a free content-management system for websites — or that it’s the world’s most popular. Everyone from small-time bloggers and businesses to major media outlets and corporations uses it. Scammers exploit poorly secured sites and publish posts with infected torrent files.
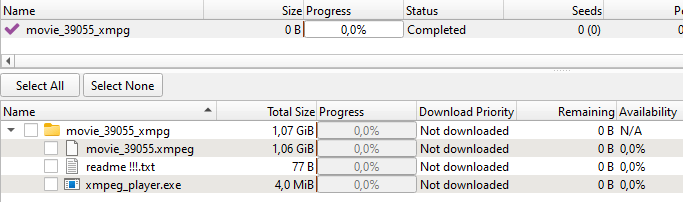
When a user downloads a torrent file from an infected site, they get a small folder that contains what looks like a movie file with the .xmpeg extension. You can’t open a file in that format without a “special media player”, which is conveniently included in the folder. In reality, the “player” is a Trojan installer.
Recently, Efimer has also started spreading through phishing emails. Website and domain owners receive emails, purportedly from lawyers, falsely claiming copyright infringement and demanding content removal. The emails say all the details are in the attachment… which is actually where the Trojan is lurking. Even if you don’t own a website yourself, you can still receive spam email messages with Efimer attached. Threat actors collect user email addresses from WordPress sites they’ve previously compromised. So, if you get an email like this, whatever you — don’t open the attachment.
How Efimer steals your crypto
Once Efimer infects a device, one of its scripts adds itself to the Windows Defender exclusion list — provided the user has administrator privileges. The malware then installs a Tor client to communicate with its command-and-control server.
Efimer accesses the clipboard and searches for a seed phrase, which is a unique sequence of words that allows access to a crypto wallet. The Trojan saves this phrase and sends it to the attackers’ server. If it also finds a crypto wallet address in the clipboard, Efimer discreetly swaps it out for a fake one. To avoid raising suspicion, the fake address is often very similar to the original. The end result is that cryptocurrency is silently transferred to the cybercrooks.
Wallets containing Bitcoin, Ethereum, Monero, Tron, or Solana are primarily at risk, but owners of other cryptocurrencies shouldn’t let their guard down. The developers of Efimer regularly update the malware by adding new scripts and extending support for more crypto wallets. You can find out more about Efimer’s capabilities in our analysis on Securelist.
Who’s at risk?
The Trojan is attacking Windows users all over the world. Currently the malware is most active in Brazil, Russia, India, Spain, Germany, and Italy, but the scope of these attacks could easily expand to your country, if it’s not already on the list. Users of crypto wallets, owners of WordPress sites, and those who frequently download movies, games, and torrent files from the internet should be especially vigilant.
How to protect yourself from Efimer
The Efimer Trojan is a real jack-of-all-trades. It’s capable of stealing cryptocurrencies, swapping crypto wallets, and it poses a serious threat to both individuals and organizations. It can use scripts to hack WordPress sites, and is able to spread on its own. However, in every case, a device can only be infected if the potential victim downloads and opens a malicious file themselves. This means that a little vigilance and a healthy dose of caution — ignoring files from suspicious sources at the very least — is your best defense against Efimer.
Here are our recommendations for home users:
- Use a robust security solution that can scan files for malware and warn you against opening phishing links.
- Create unique and strong passwords. And no, storing them in your notes app is not a good idea. Make sure you use a password manager.
- Use two-factor authentication to sign in to crypto wallets and websites.
- Avoid downloading movies or games from unverified sites. Pirated content is often crawling with all kinds of Trojans. Even if you choose to take that risk, pay close attention to the file extensions. A regular video file definitely won’t have an .exe or .xmpeg extension.
- Don’t store your seed phrases in plain text files. Trust a password manager. Read this article to learn more about how to protect your cryptocurrency assets.
What other threats lurk in the crypto world:
 cryptocurrencies
cryptocurrencies