Good old e-mail isn’t the sexiest offering in the digital world, but amid a whole bunch of newer apps and services — the instant messengers, the social networks — it’s standing its ground as an essential tool for modern-day life. Most of us still have to use e-mail, at the very least to be able to register new accounts for all those services, apps, and social networks out there.
That need is exactly why e-mail logins are a coveted prize for attackers. In this post we’ll explain how some crooks use phishing to get hold of them.
Phishing letters — the most common e-mail hacking tactics
The vast majority of scam letters made to steal e-mail login names and passwords look like messages originating from the services we use for e-mail. When targeting home users, phishers mimic popular webmail services. And when attempting to hack corporate accounts, they pretend to be your work e-mail service — in this case the sender is simply the mail server.
Popular mail services are imitated much more often. Scammers try to make such letters as convincing as possible. The deception toolkit is the standard one: a sender’s address that looks much like the real one, logos, headers and footers, links to official resources, a plausible layout, etc.
As for the corporate accounts, scammers often send phishing letters disguised as messages from corporate server or public e-mail services to shared addresses (including those used by administrators), but sometimes such letters reach the mailboxes of individual employees whose addresses have somehow ended up in spam databases.
Companies that want to be taken seriously, large ones in particular, maintain e-mail servers of their own. The logins and passwords for such accounts are also appealing to attackers. Their messages are often betrayed by less-than-perfect appearance — sender addresses from free webmail services, spelling errors, etc. — but even such letters may be taken by inexperienced employees for the real thing.
In case of targeted attacks on a specific organization, the scammers usually collect as much information about it as they can in advance to make their letters as convincing as possible. For a touch of credibility and uniqueness, they may build the victims’ e-mail addresses into phishing hyperlinks, so that when the fake page is visited the address is already there, and only the mailbox password remains to be entered.
Phishing letter variants
Simple text with request for information
Scammers simply contact users on behalf of mail services on various pretexts and request users send them e-mail addresses, passwords and other information. Users are usually urged to reply to an e-mail address that is different from that of the sender.
This phishing letter type was popular enough until scammers mastered more effective personal information theft methods.
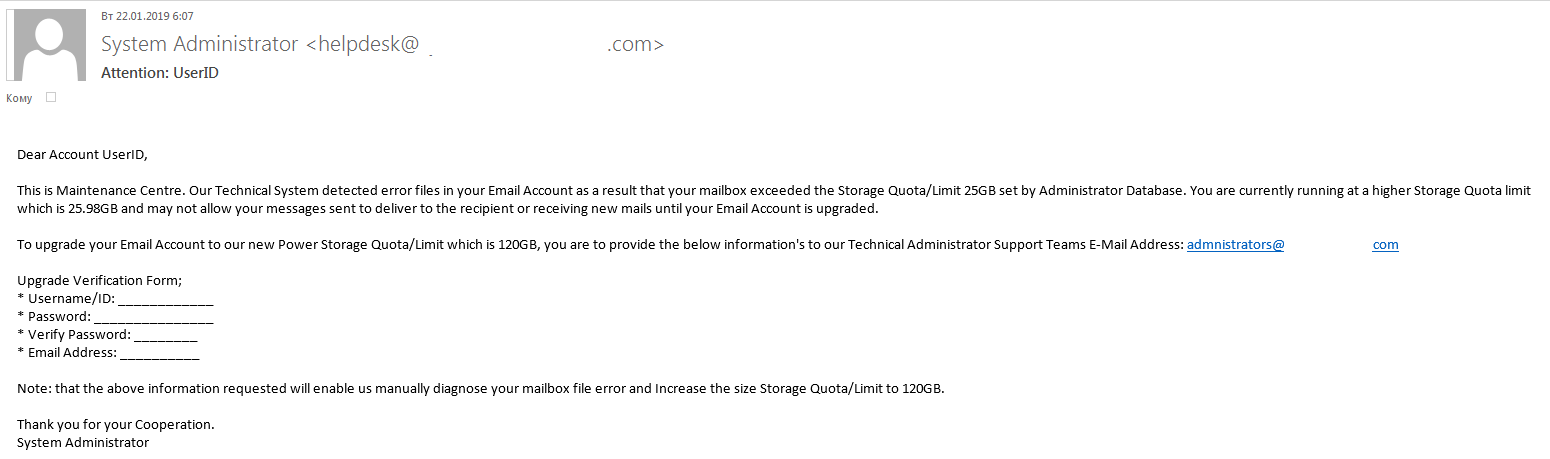
Phishing letter with a text request for account information, including password. Never send anything in response to such requests
Letter with a link to a phishing website
Phishing messages with links are currently the most common type. Scammers may use infinite numbers of pregenerated links, shuffle them from letter to letter in the same mail blast, create phishing pages that appear very much like legitimate ones, and automate collection and processing of stolen data.
But those links clearly betray a scam, leading to domains totally unrelated to the purported organizations, or using misspelled domain names styled to look like the legitimate ones. That’s why intruders try to conceal the addresses their links lead to. They do so by using clickable, hyperlinked text or images. Such text links may include phrases like “Update your mailbox.” In other cases, the text part of the link will feature the real mail service address, while the actual link will direct user to a phishing website. Many users won’t see the difference unless they check the links before clicking.
Phishing attachments
Phishing letters may also contain attachments — typically HTML, PDF, or DOC files.
Attachments in DOC and PDF formats often contain both the body of the phishing message and the scam link. Attackers opt for this tactic when looking to make the actual text of the letter itself as short and as much like legitimate correspondence as possible to bypass spam filters.
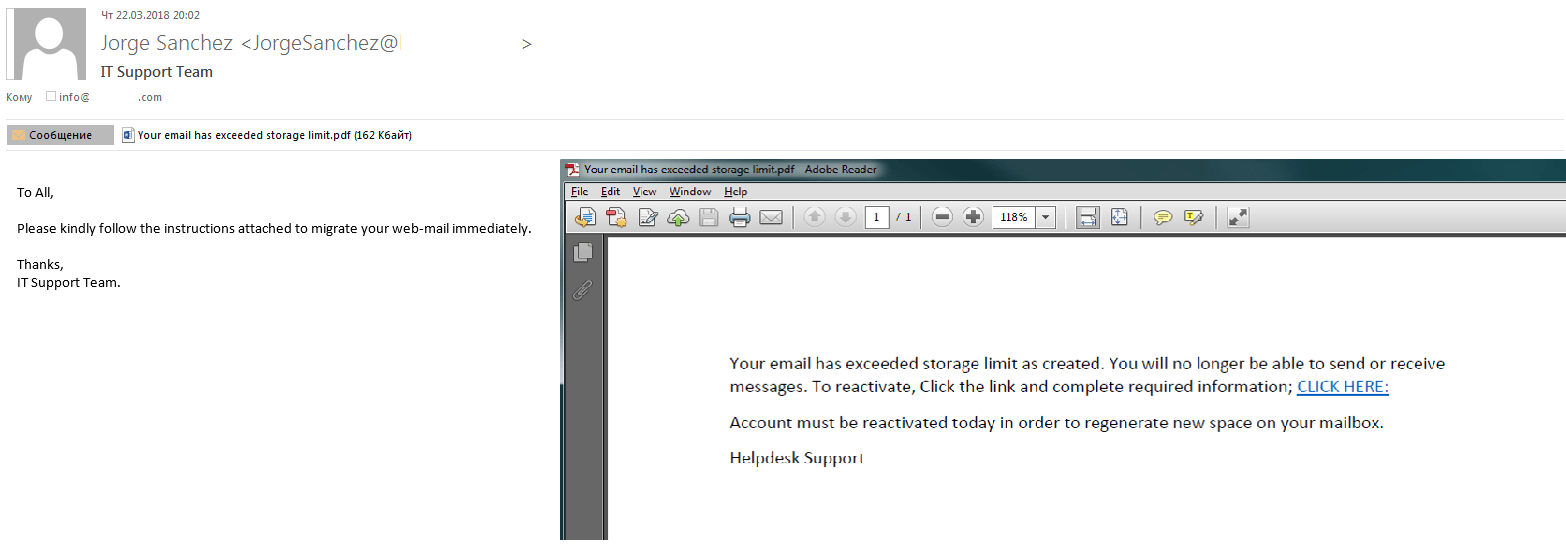
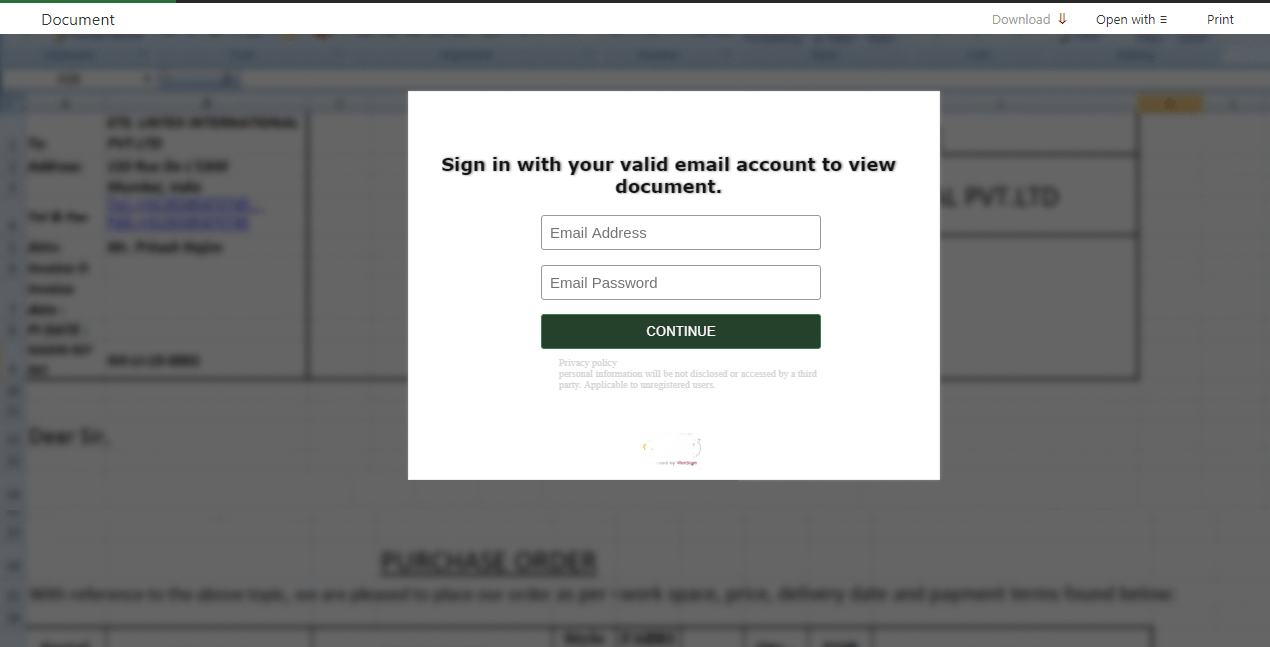
Some phishing letters come with PDF or DOC attachments with links to phishing sites inside the attached file
HTML files are used instead of links — the HTML attachment is in fact a ready-made phishing page. From the scammers’ point of view, the advantage is that the attached HTML file is fully functional — no need to post it to the Internet — and has all the elements they need for the scam.
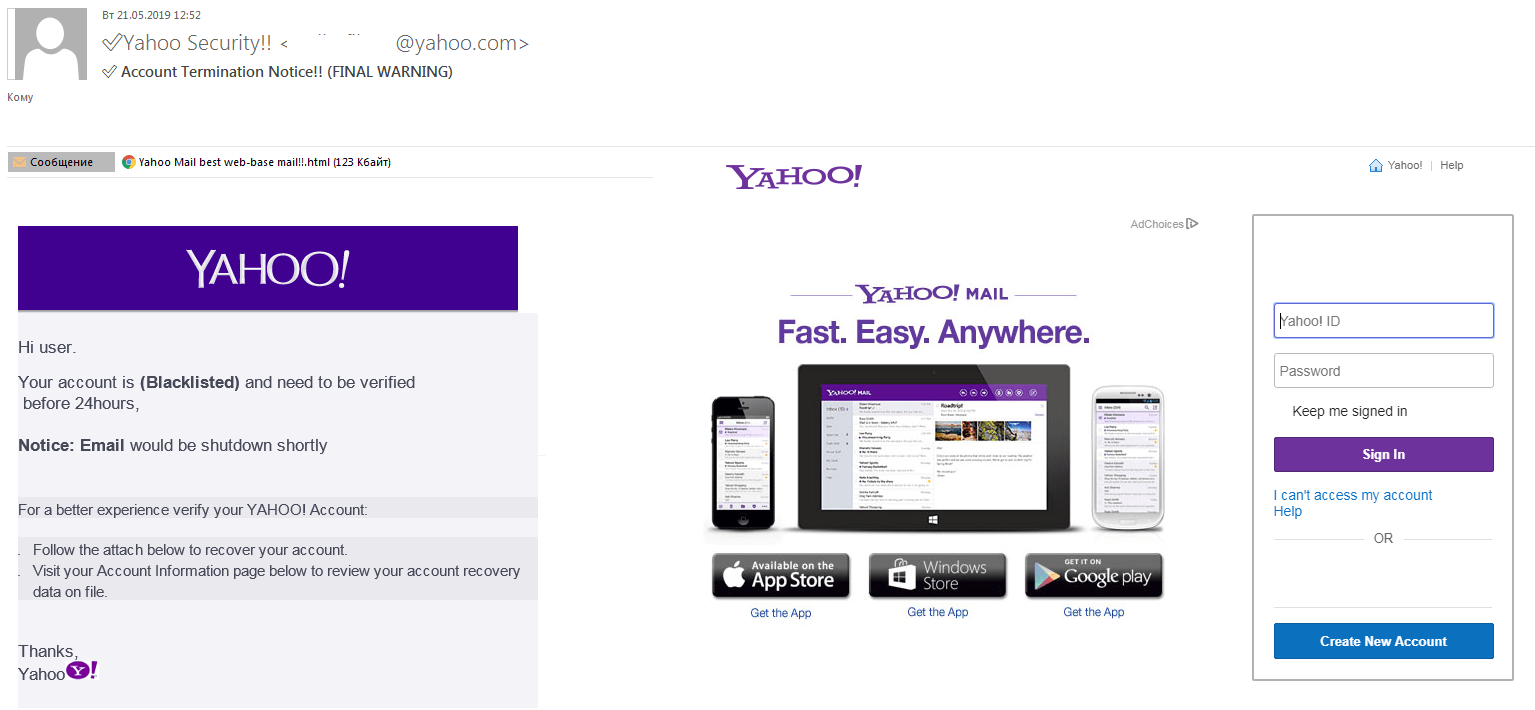
The login/password entry form is contained in the phishing letter itself. Never enter anything into something like this
Topics of phishing letters
Account problems
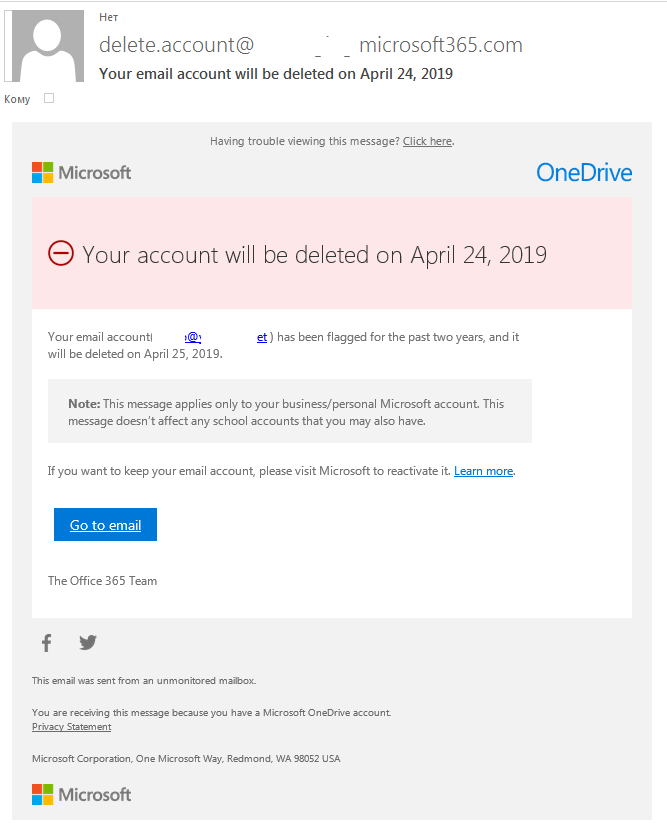
As regards the text of the letters, most of them begin by suggesting there is a problem with the victim’s e-mail account: storage limit reached, letter delivery problem, unauthorized login, spamming accusations, alerts of other violations, and so forth.
The letter normally tells the user how to deal with the problem — mostly by confirming or updating account data by following a link or opening an attachment. To frighten the recipient, it says if they don’t follow the instructions, the account will be blocked or deleted.
In almost every case, the letter sets a time frame for response, somewhere from several hours to several weeks. Usually, it’s 24 hours — both credible and not long enough to let the victim relax and forget about the letter.

“Your account will be deleted within 24 hours due to spamming.” Threats and time limits are typical phishing tricks
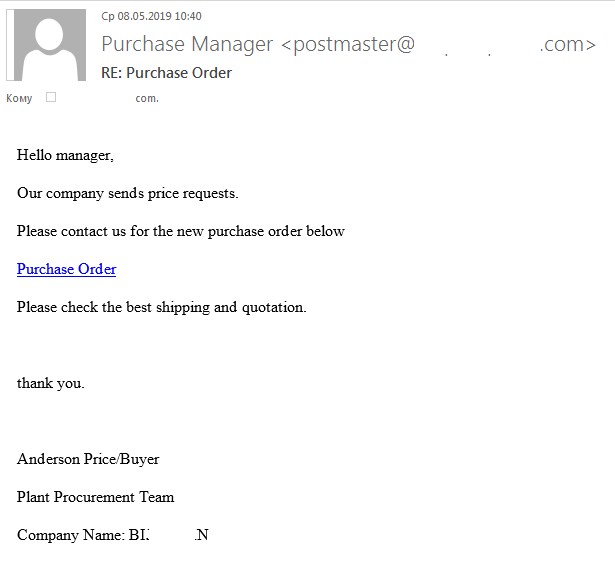
Imitation of business correspondence
Sometimes, atypical phishing letters target e-mail accounts. The text of such messages may make no reference at all to e-mail or account data. The letter may look quite like real business correspondence.
We should mention that the volume of fake business letters used for phishing has grown in the past few years. Messages of this type are usually used to deliver harmful attachments, but some of them also phish for personal data. A regular user may have a hard time detecting a phishing letter — cybercrime counts on that.
Some users will never suspect the fraud and will follow the link to log in and view a nonexistent document.
Phishing page variants
Now that we are done with the format and content of letters, let us see what phishing webpages may look like and speak about the elements to pay attention to so you can detect fraud.
The first thing deserving close attention is the link address. The address can betray a scam right away. Typical signs of fraud include:
- domains unrelated to the sending organizations,
- organization or Web service names in the address path instead of in the domain, for example, www.example.com/outlook/,
- spelling errors,
- strings of random symbols in the link address,
- symbols from other languages that look similar to the basic Latin alphabet — ç instead of c, á instead of a and so forth.
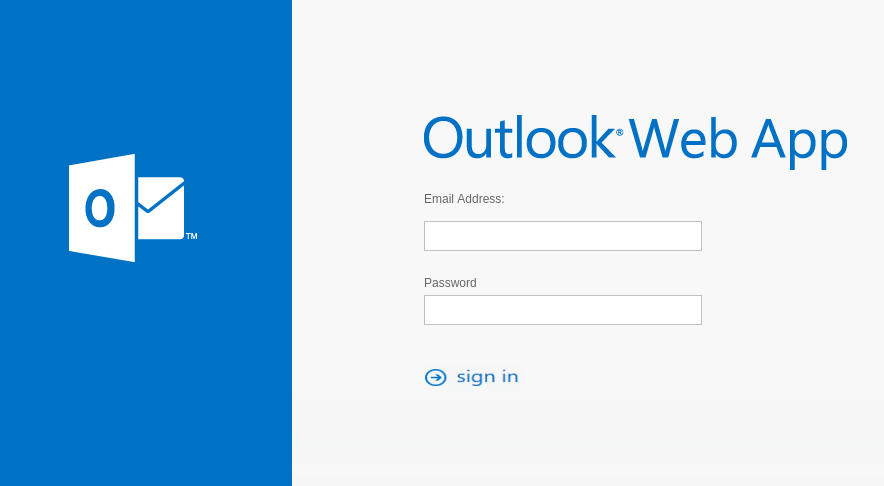
Just as with letters, phishers try to make fake webpages as much like the real ones as they can. But details always get left out — although unfortunately, not all users are able to see them.
That part is easy to understand; few people recall the exact appearance of the official homepage of their online services. So, to create a convincing phishing page it is often enough to use key characteristic elements: color scheme, logo, etc.
For phishing pages designed to steal free webmail logins and passwords it is typical to feature links to several webmail services on the same page.
As soon as any of them is clicked, a window pops up that looks like sign-in page for the relevant service. In this way, scammers can collect data for several kinds of account using just one page, rather than creating separate pages for each.
Phishers can reach even more potential victims by, instead of pretending to represent a specific mail service, using letters (on any general subject, for example, the aforementioned business correspondence option) that link to a phishing page with a choice of the most popular webmail services for users to pick the ones they need.
The time-limit trick we mentioned when discussing phishing letters is sometimes used on phishing pages, too. As soon as a user opens the scam page, it begins a visible countdown of the time remaining for the credulous user to enter their data.
When a victim submits data through a phishing page, the results vary. Some websites turn inaccessible or return error messages. Others say the user entered incorrect data and ask them to try again.
Probably the most dangerous scenario of all is gaining momentum of late. As soon as the data is submitted, the phishing page redirects the user to the real sign-in page of the webmail service in question. The user figures there was a glitch, enters the login/password pair again, successfully this time, and forgets anything weird ever happened.
Detecting phishing letters
- If the sender’s address domain does not belong to the alleged sender’s organization — and particularly if the mailbox is registered with one of the free webmail services — the letter is a scam. Official mail always comes from official addresses.
- If the letter features links to click, unrelated domains, spelling errors, special symbols, and so forth, you are looking at a fraud.
- If the letter says there are unexpected problems with your account and demands you follow a link and log in before time runs out, that letter comes from scammers.
It is useful but not strictly necessary to remember all these things and pore over every letter you receive. Instead, use a robust antivirus product to help manage phishing and other online threats for you.
 phishing
phishing