Your snapshots are, quite literally, the keys to your private life. Your gallery holds your future plans, financial secrets, cat pictures, and sometimes even things you’d never share with anyone. But how often do you truly think about protecting those images? We hope that ever since you heard about the SparkCat cross-platform stealer, you’ve been pondering it more often than usual.
Now we’ve discovered that Trojan’s little sibling, which we’ve affectionately named SparkKitty. But don’t let the cute name fool you — behind it lies a spy that, like its older brother, aims to steal photos from its victims’ smartphones. What makes this threat unique, and why should both Android and iPhone users prick up their ears?
How SparkKitty makes its way onto devices
The stealer spreads in two ways: (i) in the wild — that is, across the untamed parts of the internet; and (ii) through official app stores like the App Store and Google Play. Let’s break this down.
Official app stores
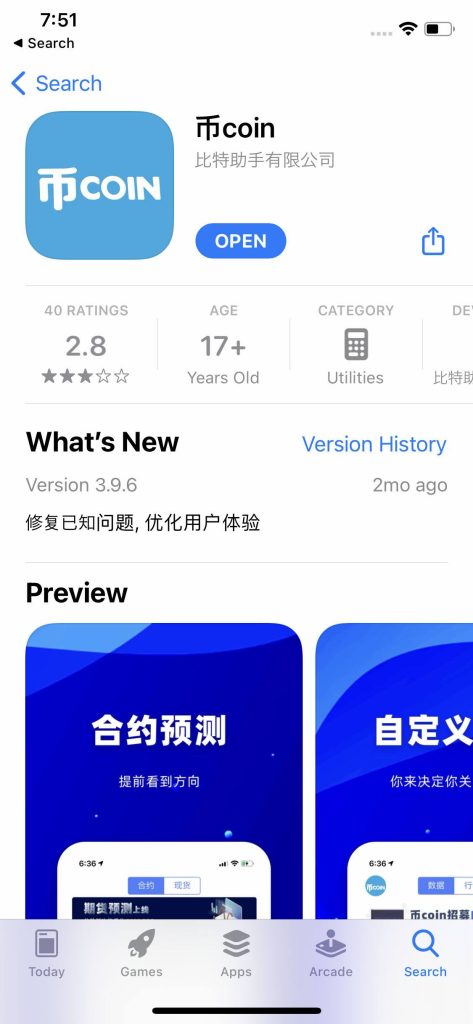
In Apple’s App Store, the malware was lurking inside the 币coin app — designed for tracking cryptocurrency rates and trading signals. We’re not sure exactly how this suspicious spy activity ended up in the app. It’s possible there was a supply-chain compromise, and the developers themselves weren’t aware of SparkKitty until we notified them. But there’s also a second possibility: the developers deliberately embedded the stealer into the app. Regardless, this is the second time we’ve seen a Trojan sneak into the App Store, and we’ve alerted Apple about it. SparkCat was the first instance.
It’s a different story with Google Play: malicious apps pop up on a regular basis, and we frequently cover these threats on Kaspersky Daily. This time, we detected malicious activity in a messaging app that includes crypto-exchange features. This is a popular app that’s been installed more than 10 000 times, and was still available in the store at the time of the study. We’ve contacted Google to warn them about the threat.
Suspicious links in the wild
That said, the attackers have been much more creative this time in spreading the malware out in the wild. Once, during a routine review of suspicious links (we click them so you don’t have to!) our experts uncovered several similar pages distributing a TikTok mod for Android. One of the main things this mod did was call additional code. “That looks suspicious”, we thought. And we were right. The code contained links displayed as buttons within the app, all directing users to an online store called TikToki Mall, which sold a variety of items. Unfortunately, we couldn’t determine if the store was legitimate or just a big trap — but one interesting fact stood out: TikToki Mall accepts cryptocurrency payments, and you need an invitation code to sign up and pay for any item. We didn’t find any further suspicious activity at this stage, and no traces of SparkKitty or other malware.
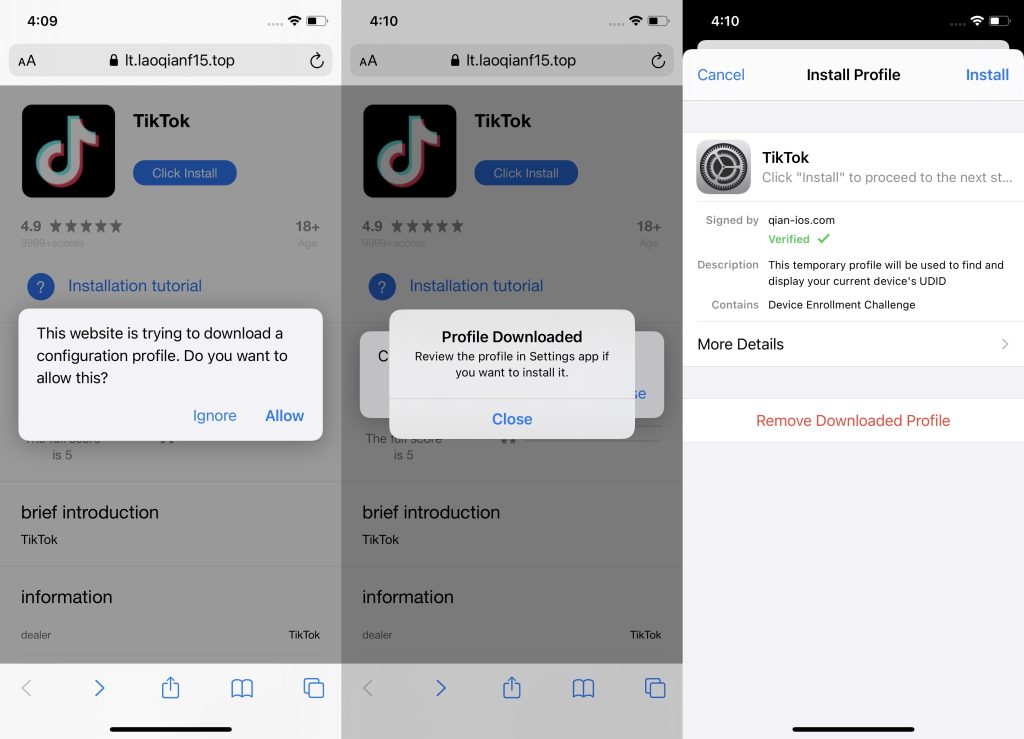
So we decided to take a different approach and see what happened when we tapped these same suspicious links from an iPhone. This led us to a page that vaguely resembled the App Store, which immediately prompted us to download the “TikTok app”.
iOS doesn’t allow users to download and run applications from third-party sources. However, Apple provides so-called provisioning profiles to every member of the Apple Developer Program. These allow installing custom applications not available in the App Store on user devices, such as beta versions or apps developed for internal corporate use. Attackers exploit these profiles to distribute apps that contain malware.
The installation process differed slightly from the usual procedure. Typically, in the App Store, you only need to tap Install once, but in this case, installing the fake TikTok required additional steps: downloading and installing a developer provisioning profile.
Naturally, this version of TikTok didn’t have any funny videos; it was just another store, similar to the Android version. While seemingly harmless, the iOS version requested access to the user’s gallery every time it launched — and that was the catch. This led us to discover a malicious module that sent images from the infected phone’s gallery, along with device information, to the attackers. We also found its traces in other Android applications. For the technical details of the story, check out our full report on Securelist.
Who’s at risk?
Our data shows that this campaign primarily targets users in Southeast Asia and China. That doesn’t mean, however, that other countries are beyond the reach of SparkKitty’s claws. The malware has been spreading since at least early 2024, and over the past year and a half attackers have likely considered upscaling their operation to other countries and continents. There’s nothing stopping them. What’s more, it’s not just the TikTok mod you should worry about; we’ve also found malicious activity inside various gambling and adult games, and even crypto-related apps.
If you think these attackers are just interested in admiring your vacation photos, think again. SparkKitty uploads each and every one of your snapshots to its command-and-control server. Those images could easily include screenshots of sensitive information like crypto wallet seed phrases, allowing these bad actors to steal your cryptocurrency.
How to protect yourself from SparkKitty
This Trojan spreads in many ways, and protecting yourself from every single one is a tough challenge. While the golden rule of “download apps from official sources only” still applies, we’ve found traces of this stealer in both Google Play and the App Store — places where apps are supposedly vetted and 100% safe. So what can you do about that?
We recommend focusing on securing your smartphone’s gallery. Naturally, the most foolproof method would be to never take photos or screenshots of sensitive information, but that’s virtually impossible nowadays. There’s a solution: store valuable photos in a secure vault. With Kaspersky Password Manager, you can only view and send protected, important photos after entering the main password, which only you know. Note that the protected content is not confined to just one device. The password manager can sync information between smartphones and computers. This includes bank-card data, two-factor authentication tokens, and anything else you choose to store in Kaspersky Password Manager – including your photos.
It’s also crucial to check your smartphone right now for any of the infected apps we’ve discovered; the extended list is available on Securelist. For Android, Kaspersky for Android can help with this — it’ll find and remove malware for you. On iPhone, due to the closed architecture of iOS, our security solution can’t scan for and delete previously installed infected apps, but it will prevent any attempts to send data to the attackers’ servers and warn you about them.
And if you opt for a Kaspersky Premium or Kaspersky Plus subscription, you get Kaspersky Password Manager along with your security solution.
Follow our Telegram channel to stay up to date on the latest cyberthreats, and make sure you’re storing your photos safely.
Learn about other malware you need to watch out for to keep your smartphone safe:
 stealers
stealers

 Tips
Tips