
Security Week 40: the ‘not-really-a-vulnerability’ in WinRAR, an ancient bug in Firefox, and the oops!-update by Microsoft
What is the difference between real and theoretical threats?
698 articles

What is the difference between real and theoretical threats?

Have you ever considered your smart office from an IT security viewpoint? Did it occur to you that by equipping your office with devices designed to provide life’s comforts, cybercriminals are handed even more opportunity to gain access to your corporate information and even to cause physical damage?

Today’s smartphones are full-fledged computers much more powerful than the desktops you used 10 years ago. Your device is very likely to contain data the cybercriminals are after, like banking data.

Today’s weekly news digest covers the stories about various mistakes in coding, and how they can be used for different purposes, including earning money.

Your legitimate copy of Angry Birds 2 may be infected with malware that steals your private data. How could this happen?

Cyber-literate users possesses a variety of good habits, which protect them online and offline. What are these traits?

A virus damaging hardware is one of the most widely believed myths in the infosec domain. And, at the same time, it’s the most non-standard one. And it’s not totally a myth, after all.

Threatpost published a fairly detective-like story earlier this month about an attacker who was able to compromise a Bugzilla, steal bug-related data, and turn it into an exploit.

The new trend on IFA 2015 is all about integrity and security. Meet Kaspersky Lab’s observations from the trade show.
Headlines raise alarm: the greatest hack in history finally reached iOS. Is that really so and who are the potential victims?

The rulebook for freethinking people: how not to get made the next time you log on Ashley Madison or buy goods in a sex shop online.

They teach a lot of things in schools, but they never tell you how to be safe in Internet. We have several simple advices on cybersecurity for you, that will help you stay away from trouble.

In-flight security made quite a lot of headlines this summer, but this time at unusual angle: the one quite surprising for an average passenger and quite expected for an IT specialist.

One can find a number of reasons why this very bug cannot be patched right now, or this quarter, or, like, ever. Yet, the problem has to be solved.

Once more into a breach: 9.7 gigabytes of stolen data with users’ emails, credit card transactions and profiles leaked into the darknet.

The experience of forgetting information you trust a digital device to remember for you is called Digital Amnesia. Digital Amnesia’s impact on businesses can range from mere inconvenience to something far more serious.

In this post there are two seemingly unrelated pieces of news which nevertheless have one thing in common: not that somewhere someone is vulnerable, but that vulnerability sometimes arises from reluctance to take available security measures.

Don’t be a slowpoke, follow Dr. House’s rule: everybody lies, especially on the Internet.
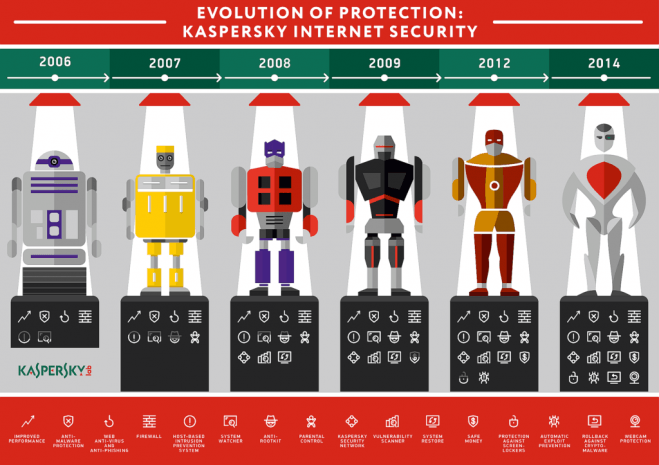
It’s not feasible to call a security solution, either for individual users or for businesses, “an antivirus.” There’s more than that.

The 2016 editions of the Kaspersky Lab product suite have enhanced privacy options for the company’s customers.
Three most important recent news with extensive commentary and trolling: nasty Android Stagefright vulnerability, new car hacks and Do Not Track 2.0 privacy initiative