
Fly safe: five tips to remember
An airborne plane is one of the safest places on the planet. However, there are rules to abide by in order to make sure the flight is a comfortable and pleasant experience.
4097 articles

An airborne plane is one of the safest places on the planet. However, there are rules to abide by in order to make sure the flight is a comfortable and pleasant experience.
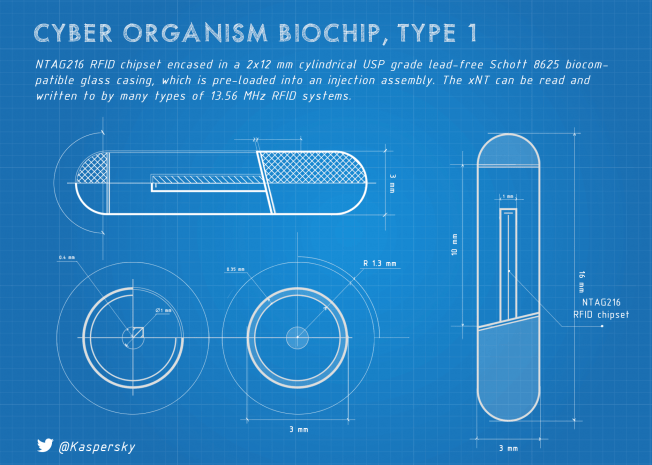
During my first two weeks of the biochip experience I had time to mull over a lot of things. In this post I’m going to touch upon the subject of form factor.

Find out about the most interesting gadgets presented at the Mobile World Congress 2015 in Barcelona

Cyberbullying is one of the unpleasant effects of hyper-socialization that the Internet as a whole – and social networks in particular – bring us. Learn how to protect your children from it.

When it comes to Mobile OSes, every 3rd option conversation these days mentions the need for some “true openness”. But do we really need this kind of openness?

Scientifically proven: video games may really boost your intellectual abilities.

Cybercriminals go at great lengths to throw researchers off their scent, but just like in the “offline” crime world they make errors and leave peculiar traces behind, making them look a bit silly, while the cyber-forensic experts get happy.

New allegations against the NSA claim the group hacked into the network of the world’s largest SIM card provider, stealing encryption keys to millions of devices.

The story of how a biochip was implanted into my hand and why I needed it.

One dollar lesson is a new interactive project by Kaspersky Lab that aims to help you stay protected from online money frauds. Learn three simple lessons right now!

Kaspersky Lab announced the immediate availability of Kaspersky Security System. The new platform is launched as an embeddable OEM component to manufacturers and vendors of comprehensive IT solutions.

Brian Donohue and Chris Brook of Threatpost discuss Kaspersky Lab’s Security Analyst Summit, which took place last week in Cancun, Mexico

It turned out that Lenovo’s laptops had been shipped with an adware called Superfish. It possibly allows eavesdropping on encrypted connections

Do you like working in open plan office? Many say no. That can be remedied by new ideas introduced by office space designers.

Kaspersky Lab researchers uncovered Desert Falcons, the first exclusively Arabic APT group, presenting their findings at the Security Analyst Summit in Cancun.

On February 16th and 17th in Cancun, Mexico, the Fourth annual Kaspersky Security Analyst Summit took place. Here are several chosen moments from the keynotes presented there.

There is a flood of appliances which could be connected – and some are connected – without a second thought as to whether or not it’s necessary or secure.
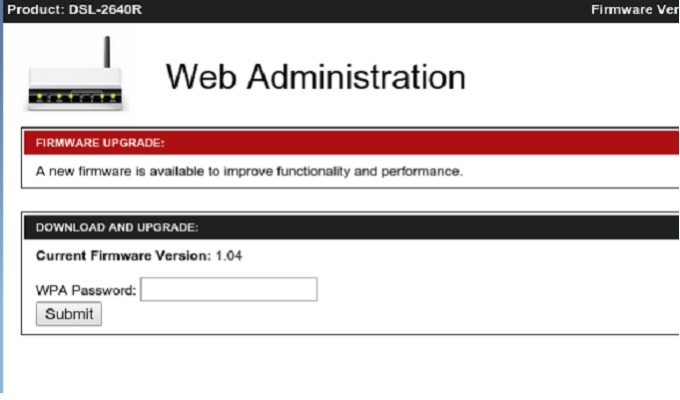
Today we discuss the most important news on information security from January.

Let’s talk about the dangers of cross-border payments with plastic cards and security flaws in payment systems architecture.

Kaspersky Lab has discovered the first APT campaign launched by Arabic speakers, operating in the Middle East.

Kaspersky Lab’s researchers have discovered what is possibly should be called “mother of all APTs”: the Equation group has already been compared to Death Star in the APT universe.