
LastPass users need to change their passwords immediately
The web service for secure password storage, LastPass, asks users to change their passwords ASAP.
911 articles

The web service for secure password storage, LastPass, asks users to change their passwords ASAP.

Cybercriminals frequently use spam as the primary channel to spread malware. Of course, this is something we should take care of.

Since the holiday season is upon us, we prepared a list of simple tips to help you minimize risks when renting a car abroad.

Ransomware is a huge problem nowadays, with new examples circulating on a regular basis. Learn how to protect yourself.

Encrypting ransomware is a relatively new, but extremely pesky, threat that is evolving at a rapid pace, becoming a more advanced problem for end-users and businesses alike. What can be done about it?

A new, Chinese-language APT has emerged, seeking geopolitical information and targeting nations in and around the South China Sea
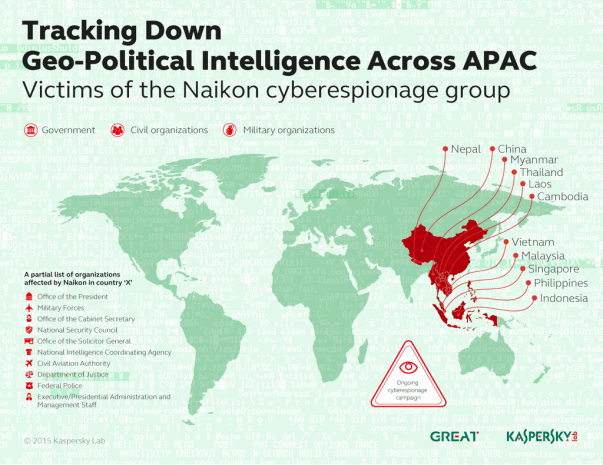
Kaspersky Lab experts have investigated one of the most active APTs (Advanced Persistent Threats) in Asia, operating specifically around the South China Sea area. It was named “Naikon” after the “nokian” User-Agent substring within an attack components’ code.

Personal smartphones and tablets are used to store working data, both personal and corporate passwords, and other sensitive information. So, it is troubling that mobile protection often lags behind.

Five lessons from the story of the Enigma cryptographic machine which are still relevant.

Mid-April in Singapore was pretty hot not only because of tropical climate, but also because of INTERPOL World – a huge conference/exhibition organized by INTERPOL to give security product vendors

Yet another APT of the ‘Dukes family’ is hitting high-profile targets, including the US government office.

Yet another Duke APT is hitting high-profile targets, including the US government office. This time it’s CozyDuke (also known as CozyBear, CozyCar or “Office Monkeys”, in honour of the video it employs as a decoy).

The annual RSA Conference in San Francisco, California of Internet-of-things insecurity and how no amount of money can fix computer security

The necessity of a product that is positioned in-between the enterprise-level suites and home-users solutions became apparent only a few years ago.
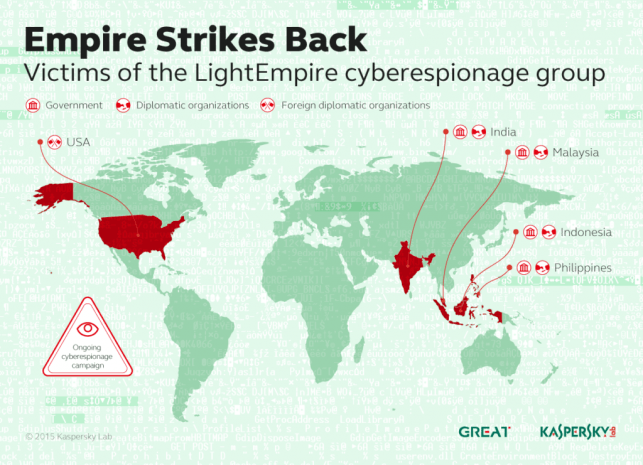
Kaspersky Lab experts have discovered a new APT campaign that targets government institutions, mainly in the APAC region. It was named “Hellsing” after the string containing the project directory name found within the attack components’ code.

Security is a tough matter for small businesses for multiple reasons; startups and small entities tend to save on their IT wherever possible, and that’s where security failures are common.
The cybersecurity has become the everyone’s business, and it raises the demand for continuous update of information for everybody, both high-level security professionals and common corporate users. And especially for the latter, since it is them criminals attack most of the time.

An annoying story of ‘free’ WiFi hotspots by St. Petersburg-based Smart WiFi. Nothing is for free, though, as you end up paying with your vk.com credentials

As cybercrime keeps focusing on profit, the share of plainly malicious spam, spreading out Trojans, phishing links, etc., will grow.

A large-scale “pharming” campaign targeting home routers took place in South America, the latest in a trend Kaspersky Lab’s experts have been monitoring for awhile. Home routers are frequently used

Fraudsters hacked Skype and tricked people from a contact list to send them about $5,000 over the course of a few days. Skype support, local banks and the police refused to do anything.