
Cash out with ease: why and how ATMs get attacked
Remember the beginning of Terminator 2: The Judgement Day where John Connor is shown hacking an ATM with an Atari Portfolio?
31 articles

Remember the beginning of Terminator 2: The Judgement Day where John Connor is shown hacking an ATM with an Atari Portfolio?

2015 proved: it’s possible to hack a connected car remotely. But is it as dangerous as it seems?

In this post there are two seemingly unrelated pieces of news which nevertheless have one thing in common: not that somewhere someone is vulnerable, but that vulnerability sometimes arises from reluctance to take available security measures.

Recently we wrote about the Jeep Cherokee hack incident. At Black Hat security researchers Charlie Miller and Chris Valasek finally explained, how exactly the now-famous Jeep hack happened.

Threatpost security reporters Chris Brook and Brian Donohue discuss the Github DDoS, Dyre banking malware, privacy threats, hacking and more

June was a busy month with hacks and data breaches, privacy, cryptography, and mobile security news, and an update on OpenSSL Heartbleed.
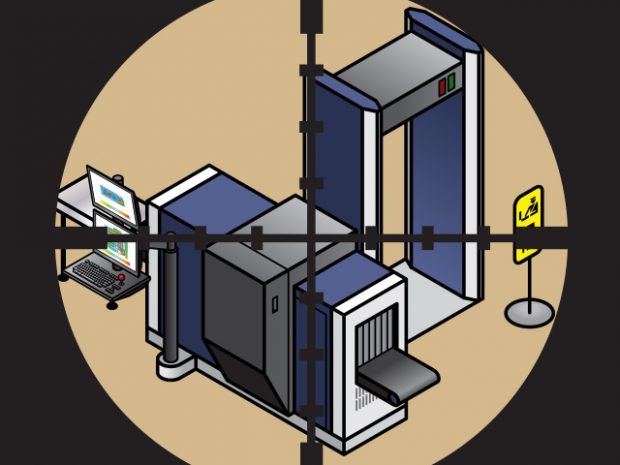
If you try to think of the most secure place in the world, you probably think of some military bunker or U.S. President’s hiding vault. But for us ordinary folks,

No doubt it has been a crazy week for anyone even remotely interested in Bitcoin. Mt. Gox, once the largest Bitcoin exchange marketplace out there, has shut down, putting a

The Syrian Electronic Army (SEA) has struck again, this time attacking the account records of more than a million Forbes readers and contributors. A total of 1,071,963 users were affected

For as long as I’ve been working in the security industry, which – in the spirit of full disclosure – hasn’t been a very long time, I have been shocked