Kaspersky Lab discovered Asacub, a banking trojan which started actively attacking Android users in January. Our experts managed to track its evolution step-by-step.
A banking trojan is a type of malware which is installed a mobile device and employs certain techniques to steal money from the user’s credit cards. Recent versions of Asacub does it by luring a user into submitting credit card credentials via phishing screens. Obviously, this data is not going to a legitimate bank.
At first, researchers suggested the banking trojan was targeting Russia and Ukraine exclusively, due to the fact that the phishing resembled the login screens of some Russian and Ukrainian banks. However, further investigation allowed Kaspersky Lab researchers to identify an additional version intended for US users as another phishing screen boasted the logo of a major American bank. Besides fake login screens, the malware does not resort to other means of siphoning credit card data; so it seems that Asacub’s creators targeted only select banks.
Nevertheless, Asacub is a lot more than a simple phishing scam, despite the fact that it used to be an even simpler piece of malware in its early days — its evolution started from the lowest ranks of the malware hierarchy.
The first iteration of the malware, whose family is detected by Kaspersky Lab’s products as ‘Trojan-Banker.AndroidOS.Asacub’, was discovered by our research team in June 2015. Back then it was a typical sample of a phishing program, remotely managed from a command and control server.
Banking Trojans: mobile’s major cyberthreat #malware https://t.co/qWtgJjbCjq pic.twitter.com/qpyQEJvYHG
— Kaspersky (@kaspersky) September 30, 2015
Installed on the affected device, the first version of Asacub was able to send certain information, including the list of apps, browser history and the contact list, to a remote C&C server. The early Asacub could also send SMS messages to a particular phone number and turn off the screen on demand — that was it.
A new version of Asacub was spotted in July and it had a more advanced toolset. In addition to existing capabilities, it was able to manage the cycles of C&C communication, intercept or delete text messages and upload the SMS history to a remote server.
The newer version got a handful of other capabilities: it could mute the phone, keep the CPU in an active state even if the screen was turned off, and, what is even more important, provide console access to culprits. The latter is a classic backdoor feature and is rarely used by mobile banking trojans. From that version onwards, Asacub became something more significant than a mere phishing program.
Banking #Malware is Rapidly Growing on #Android http://t.co/5ahdBLFNPX #FakeToken
— Kaspersky (@kaspersky) April 17, 2014
Asacub eventually became what it is now in September. In addition to the aforementioned capabilities, it started employing phishing screens to steal credit card data in select mobile banking apps. Moreover, it learned to forward the victim’s calls to a particular phone number, send USSD requests, download and run files from rogue URLs.
Until recently, Asacub preferred to lay low: Kaspersky Lab researchers were aware of several iterations of the malware but saw no massive attacks employing Asacub, until they were able to spot several campaigns over the Christmas holiday. Roman Unucek, one of the experts who discovered Asacub, notes:
‘The malware remained off our radar until recently, when adversaries started to actively distribute Asacub during the Christmas break, which eventually made Asacub one of the most notorious mobile threats in 2016.’
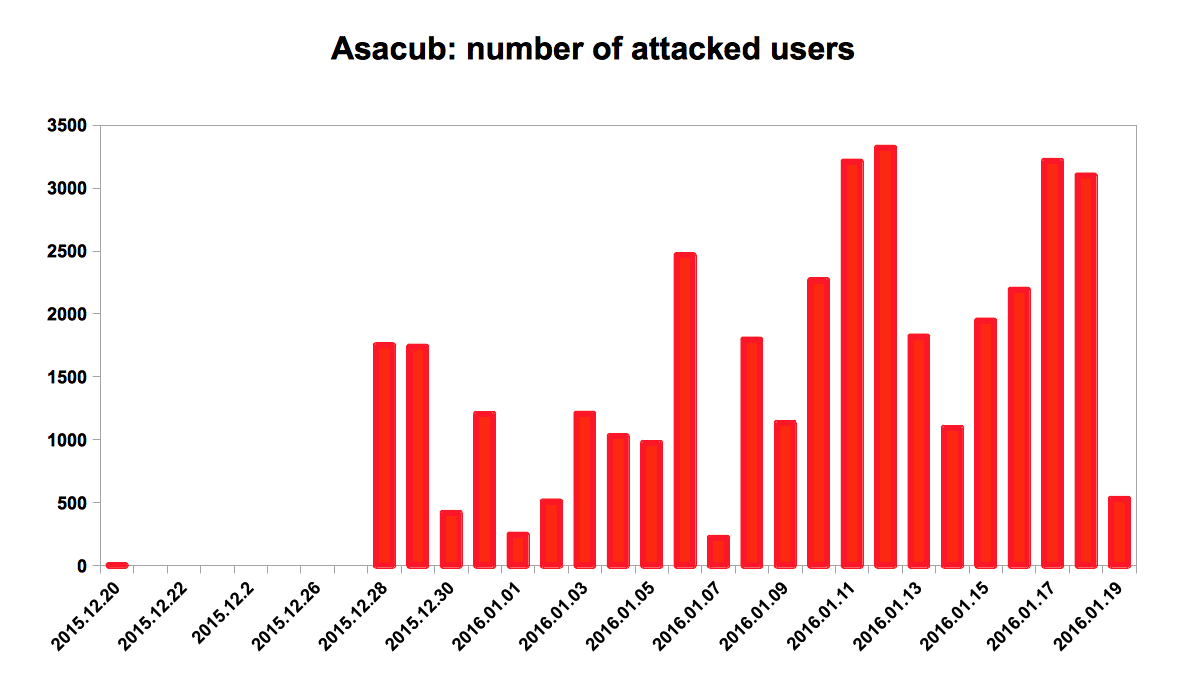
In fact, the researchers registered over 6,500 detections in the first week, which made Asacub the most active banking trojan of that week. By now there are more than 37,000 infection attempts registered.
A common spyware program, #Asacub evolved into a full-fledged banking Trojan. #security #onlinefinance
Tweet
A quick look on the Trojan’s feature list can make your hair turn grey. Having an infected Android device, Asacub gains total control over the system. It would be able to steal data (from SMS messages to banking credentials), forward calls, snap photos and even install other malware probably including ransomware.
Asacub is an all-in-one hacker asset. It could be used for phishing, malware distribution or even blackmailing. As it looks now, the adversaries are just testing out the available toolset, and there are reasons we should anticipate massive campaigns.
Shop + bank online without worrying about the safety of your financial data – it's protected by Safe Money technology http://t.co/olj2YjrfHL
— Kaspersky (@kaspersky) April 11, 2013
There is only one functional way to protect oneself from this threat: a robust antivirus. Kaspersky Internet Security for Android is capable of detecting and blocking all existing versions of Asacub. A premium version can do it on the fly. If you use a free version of the antivirus, do not forget to run regular manual scans to prevent infection.
 asacub
asacub



 Tips
Tips