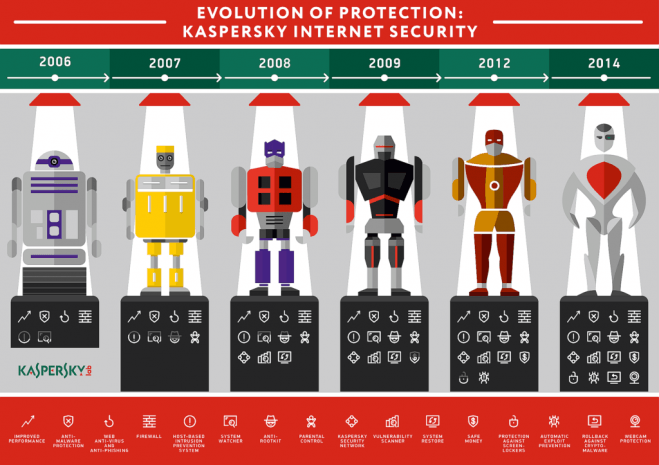
Hacking-Back: Six Justifications for Doing It and What’s Wrong With Each One
If the idea of “hacking-back” against cybercriminals who have harmed you or your company has seized you, your executive team, or your spouse as a reasonable thing to do, read
 Cybersecurity
Cybersecurity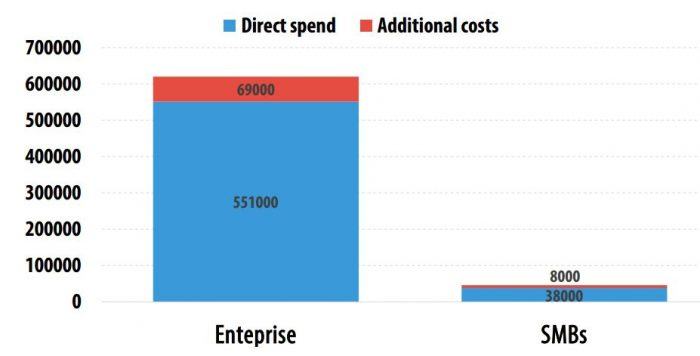

 banking trojans
banking trojans
 cybercrime
cybercrime
 password manager
password manager
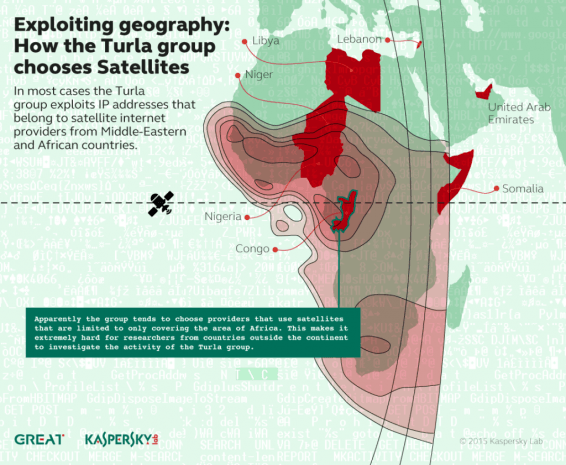
 APT
APT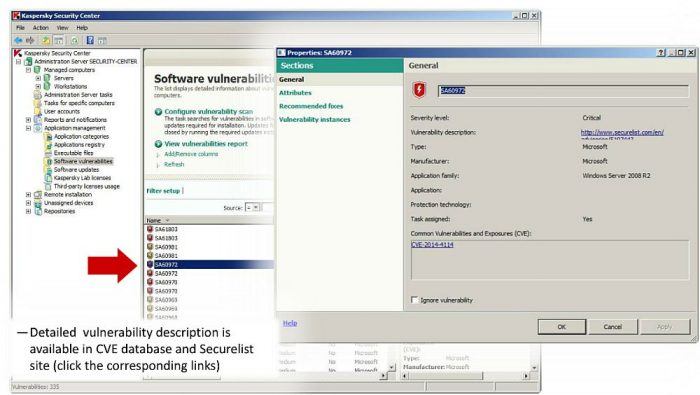


 glossary
glossary
 cyber incidents
cyber incidents